Ques- What is the significance of the following TCP header fields:
- Urgent Pointer
- Checksum
- Window Size
- Reserved bits
- Sequence Number
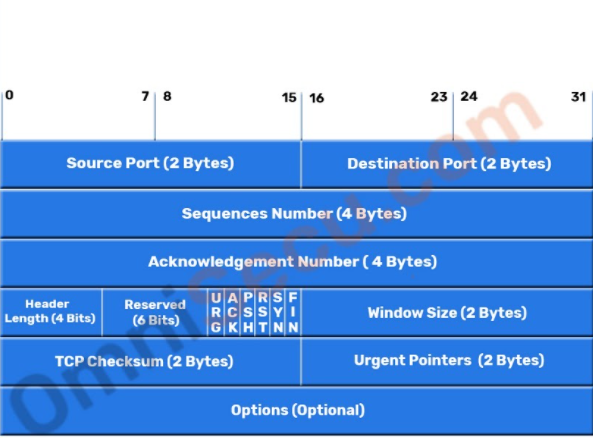
Transmission Control Protocol (TCP) Segment Header.
Sequence number
32 Bit number used for byte level numbering of TCP segments. If you are using TCP, each byte of data is assigned a sequence number. If SYN flag is set (during the initial three way handshake connection initiation), then this is the initial sequence number. The sequence number of the actual first data byte will then be this sequence number plus 1. For example, let the first byte of data by a device in a particular TCP header will have its sequence number in this field 50000. If this packet has 500 bytes of data in it, then the next packet sent by this device will have the sequence number of 50000 500 1 = 50501.
Reserved Bits
- These bits are not used.
- The 6 bits are reserved.
Window size
Indicates the size of the receive window, which specifies the number of bytes beyond the sequence number in the acknowledgment field that the receiver is currently willing to receive.
- Thus, window size is used for Flow Control.
- It advertises how much data (in bytes) the sender can receive without acknowledgement.
- It contains the size of the receiving window of the sender.
- Window size is a 16 bit field.
Checksum
- Receiver rejects the data that fails the CRC check.
- Sender adds CRC checksum to the checksum field before sending the data.
- It verifies the integrity of data in the TCP payload.
- Checksum is a 16 bit field used for error control.
Urgent Pointer
Shows the end of the urgent data so that interrupted data streams can continue. When the URG bit is set, the data is given priority over other data streams (Size 16 bits).